A penetration test is a check of your IT for IT security gaps and weak points. Here the system is checked very practically, mainly, on a technical level from the perspective of an attacker. The theory only plays a subordinate role. A penetration test is therefore an image of the actual level of protection without blurring and the influence of “security attesting” documents. The penetration test can have different characteristics, focal points and test depths. For example, a single application within a network can be the target or also the entire network.
Our penetration tests
All of our penetration tests are carried out by former hackers. We offer you a wide range of techniques, methods and realistic scenarios. Our IT security experts use real-world attack methods.
Here transparency is very important to us: If you wish, we will explain the techniques and methods used in detail after the test has been completed. The continuous development of our skills and attack scenarios in our laboratory, training programs and cooperation with a broad IT security community enable us to test your company for the latest security gaps and vulnerabilities. Our penetration testers own various IT security certifications, are regularly certified in data protection areas and are therefore trained in the confidential handling of the data found.
What differentiates us? We make the penetration test tangible. We present the status of your application or your network without complicated results analysis and in a legible form and give you several solutions to help you solve the problems found quickly and/or sustainably.
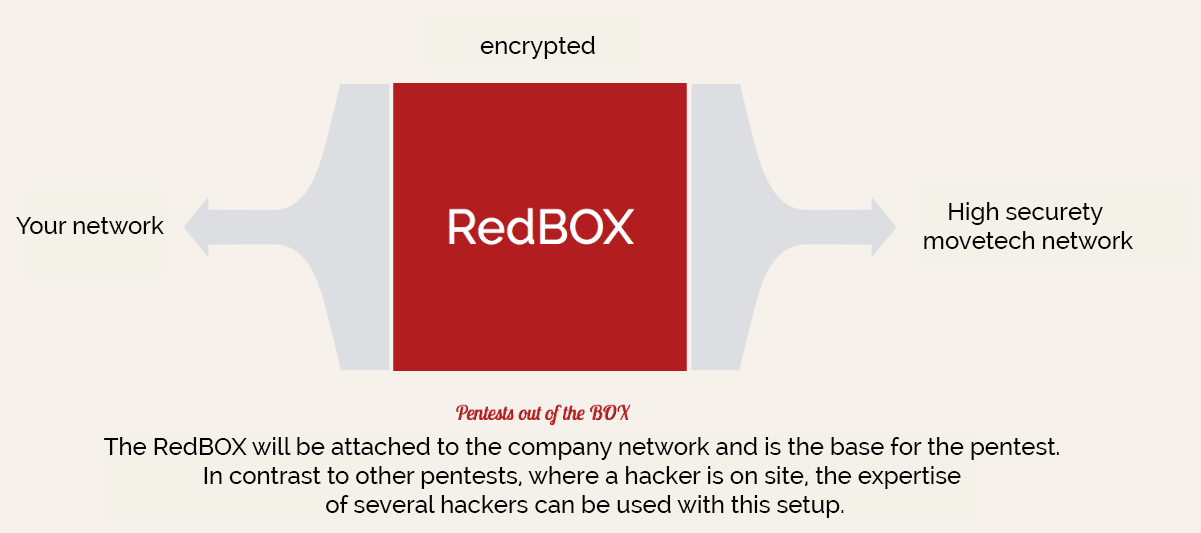
The RedBOX
Our penetration tests are run as follows:
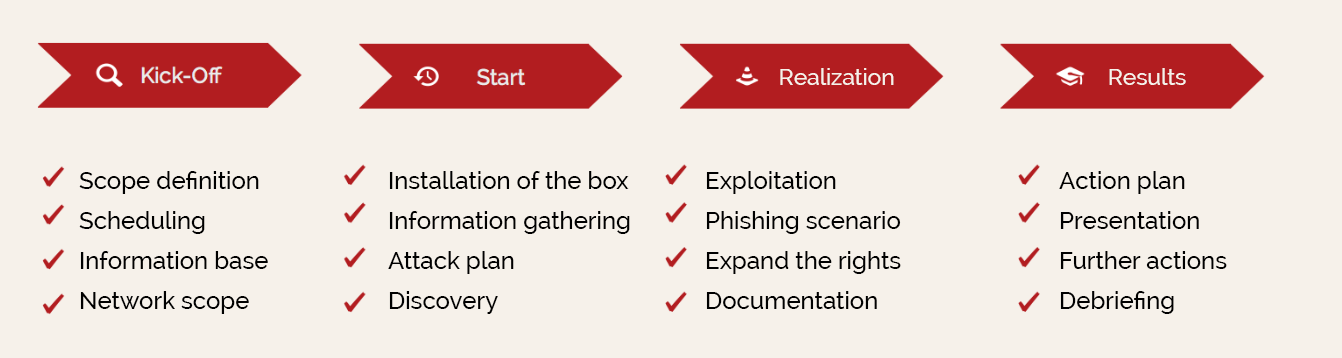
This phase determines how extensive the penetration test is and on what the focus should placed. On the basis of a small pre-check and the ideas of the client, it is decided together how the process can be designed sensibly and provide the client with the most added value. In addition, all other appointments and possible steps are defined. As a rule, this appointment takes place on site.
The penetration test starts. Our RedBOX will be installed at your location. Our penetration testers start by identifying targets within the defined area, drawing up an attack plan and collecting initial data.
In this phase, our penetration testers use their skills and “arsenal” to “exploit” the found targets, extend the rights, collect data and document the results. Every penetration test includes a phishing scenario, which—if nothing special is desired—is created by our penetration testers specifically for your company. All of this is important so that we can provide you with the most realistic results possible.

The decisive phase for you starts: Our security chief will present on site the security gaps and weaknesses found, transfer all data and uninstall our RedBOX. The resulting steps and options are also shown. The results also include a so-called action plan, which summarises the security gaps and weak points found in logical groups and suggests the resulting measures. The action plan is based on Prince2. With the help of predefined divisions based on the RACI model, measures can be planned, distributed and controlled in a comprehensible manner. The action plan is at the heart of our work. It forms the “focal point” for you to solve problems and further plan your IT security.
Books can be filled about the setup and course of a penetration test. We recommend: Call us and we will be happy to answer your questions!