Digitalisation is changing the economy and society. It supports new business models and creates opportunities for growth. However, digitalisation also comes with new challenges. That's why IT and cyber security require a strategical approach — starting with the management.
From our experience, we know that this issue is either put off or the responsibility is given over to the internal IT department or an external IT service provider. But here comes another problem that companies face internally: In most companies, IT administration is also responsible for IT security (more about that here).
This works well until there is a critical IT incident.
Many manufacturers blatantly praise their solutions. “Buy our product and you’ll be completely safe!” This is what advertisements or sales pitches tell you. Current buzzwords such as AI—artificial intelligence—and blockchain are also thrown in for good measure. Don't be fooled. What is sometimes presented as an unbreakable AI antivirus solution and comes with a horrendously high price tag can be outsmarted in merely a few hours.
Instead of these single or isolated solutions, we—and other consultants—recommend the implementation of an information security management system (ISMS for short). Generally, a SIEM (Security Incident Event Management System) makes sense, although the BSI basic protection, an ISO 27001 compliant or a correspondingly well-designed SIEM solution is also likely to be too challenging or cost-intensive for most companies.
But what matters more than anything written in any documents or certificates is the culture of your company. Instead of top-down approaches, where applications and systems are imposed on you, you'd better create a solid foundation. We call it “the mountain that is IT security”. And it can be conquered by any company.
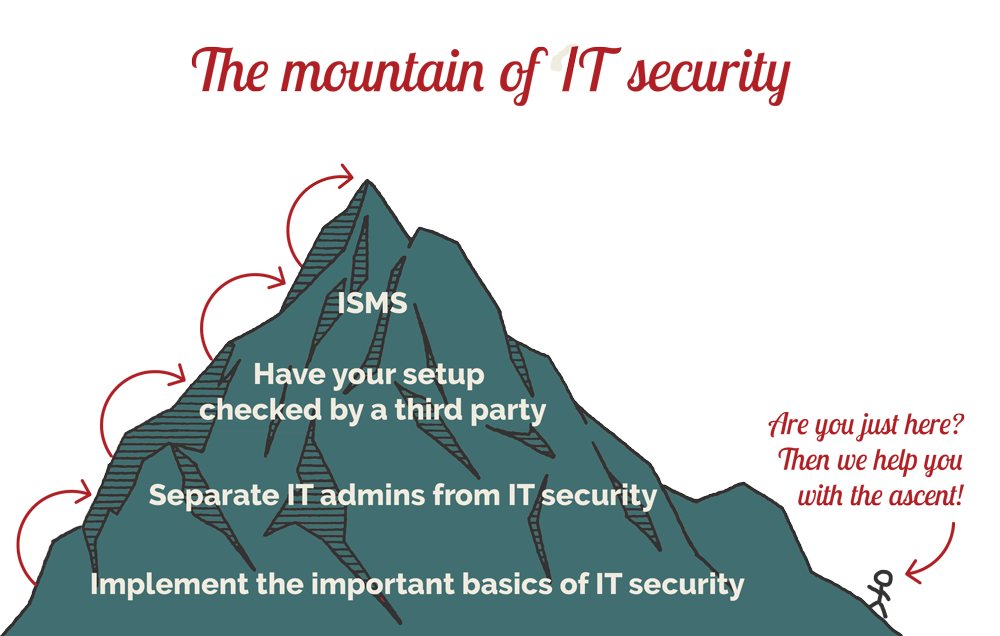
- The basis: Implement in your company the important basics of IT security. Have the compliance checked. Never rely solely on claims, but insist on thorough documentation. If your IT service provider does not manage to send you up-to-date documentation or backup monitoring for the past twelve months within one hour, he must either have damned good reasons or he has not kept any.
- Internalise the separation of IT administration and IT security. The job of the IT administrator is to keep the system running, while the IT security has to find weak points, i.e. to thwart the system. These are two different approaches and, accordingly, two departments - external or internal.
- Have your entire system checked on a regular basis. A penetration test or security checkup will show you where the weak points are — either in terms of stability or in terms of vulnerability to viruses and attacks from the perspective of hackers. The financial expenditure is not exactly marginal, but definitely only a fraction of a damage repair.
- Only now does an information security management system (ISMS) come into play. This bundles the various measures and gives them structure — IT security is thus defined as a process. It can be complicated, but it doesn't have to be. The “ISIS12”, published by the Bavarian IT security cluster, breaks down the Catalogues from the BSI into twelve relatively easy to implement steps. It is suitable for small and medium-sized companies as well as municipalities and cities. The advantage of such a procedure is not only increased IT security, but also an improved image. With the implementation of an ISMS, you set yourself apart from many competitors in the area of IT security. This also makes the step towards ISO 27001 relatively easy.
When it comes to IT protection, much-discussed “Artificial Intelligence” (AI) has so far only played a role in marketing. Attacking AI systems almost always break down defensive AI systems. That may change at some point, but in late summer 2019, AI as a means of IT security is not the means of choice.
Are you interested in conquering the Mountain of IT Security?
We are happy to help: We accompany you in climbing the steepest part or show you which aids and contacts are also useful on the way to the summit.
Yours sincerely,
Steffen Mauer